Descripción
This lab is vulnerable to DOM XSS via client-side prototype pollution. The website’s developers have noticed a potential gadget and attempted to patch it. However, you can bypass the measures they’ve taken.
To solve the lab:
- Find a source that you can use to add arbitrary properties to the global
Object.prototype. - Identify a gadget property that allows you to execute arbitrary JavaScript.
- Combine these to call
alert().
You can solve this lab manually in your browser, or use DOM Invader to help you.
This lab is based on real-world vulnerabilities discovered by PortSwigger Research. For more details, check out Widespread prototype pollution gadgets by Gareth Heyes.
Client-side prototype pollution via browser APIs writeup
Entramos en el laboratorio con el DOM Invader activado. Damos Click derecho -> Inspeccionar -> DOM Invader:
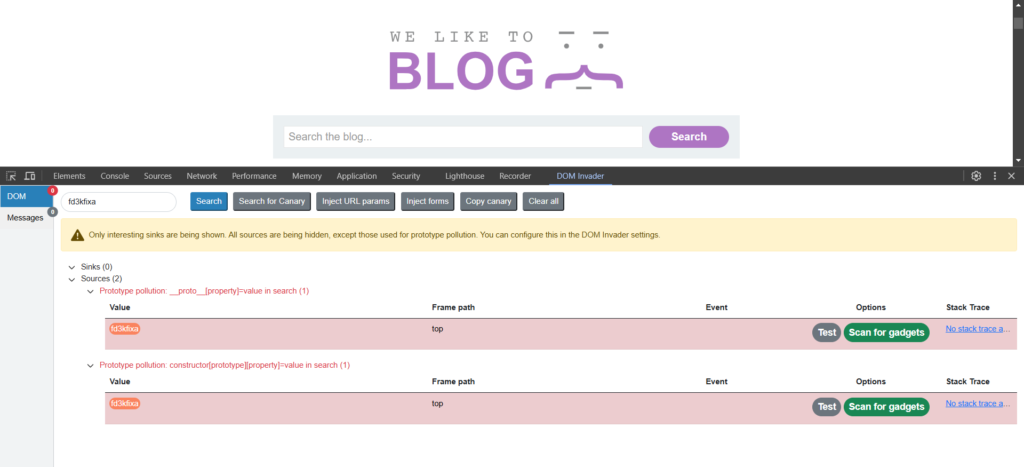
Encontramos dos posibles vulnerabilidades. Pulsamos en ‘Scan for gadgets’ de la primera vulnerabilidad y lo dejamos actuar. Cuando nos salga el mensaje de que se ha completado volveremos a la pestaña de DOM Invader y pulsaremos ‘Exploit’:

Completando el laboratorio: